With the world increasingly dependent on digital connectivity, data breaches have surged to unprecedented levels. According to Forbes Advisor, “2023 saw a 72% increase in data breaches since 2021, which led the previous all-time record.”
As businesses continue to migrate to the cloud, securing infrastructure becomes a critical concern. Built for scalability, reliability, and sustainability, AWS offers numerous multi-layered security tools that proactively defend cloud environments. Through constant monitoring and advanced automation, AWS enables organizations to mitigate security risks while maintaining operational efficiency.
Understanding the Shared Responsibility Model
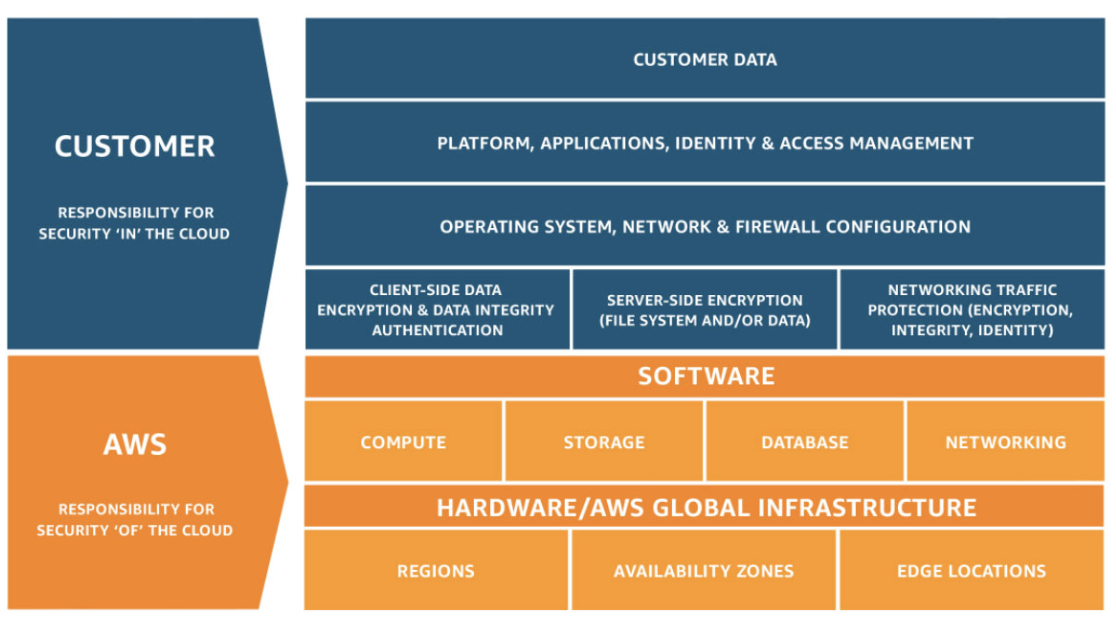
Cloud security isn’t a one-size-fits-all approach—it requires clear boundaries between what AWS secures and what your organization is responsible for. AWS fortifies the physical infrastructure, ensuring the safety of its global data centers and the underlying network. On the other side, you hold the reins when it comes to safeguarding your data, applications, and workloads. This division empowers businesses to implement security controls that align with their specific needs, without compromising the strength of the underlying infrastructure.
The Blueprint for Cloud Security: Best Practices for a Resilient Infrastructure
Elevating Security with AWS Identity and Access Management (IAM)
In an era where data breaches can have devastating consequences, managing who has access to your cloud resources is paramount. AWS Identity and Access Management (IAM) empowers organizations to define and control individual user permissions, ensuring that only the right people have access to the right resources at the right time.
One of the standout features of IAM is its integration with Multi-Factor Authentication (MFA), which adds an extra layer of security for privileged accounts. Whether you choose software-based solutions like mobile authenticator apps or hardware tokens, MFA significantly reduces the risk of unauthorized access, making your cloud environment that much more secure.
IAM isn’t just about restricting access; it also simplifies user management through federated access. With IAM, your employees and applications can authenticate to the AWS Management Console and service APIs using existing identity systems, such as Microsoft Active Directory. This integration minimizes administrative burdens and streamlines the user experience, allowing your team to focus on what truly matters—driving innovation and growth.
Additionally, AWS IAM Identity Center (formerly AWS Single Sign-On) revolutionizes how organizations manage access across multiple AWS accounts and applications. With centralized control, businesses can easily provision and deprovision access based on changing roles, ensuring that employees have the necessary access to do their jobs while maintaining tight security controls.
Navigating the Terrain of Network Security
Network security is not merely an option; it’s a fundamental necessity. AWS empowers organizations to build resilient networks that serve as formidable barriers against cyber threats. Central to this defense is Amazon Virtual Private Cloud (VPC), allowing you to carve out a secure space in the cloud, ensuring that resources are accessible only to those who need them.
With VPC, you can design your network architecture, incorporating features like Security Groups and Network Access Control Lists (NACLs). Security Groups act as virtual firewalls, controlling inbound and outbound traffic to instances, while NACLs provide additional defense by regulating traffic at the subnet level.
For organizations seeking to streamline connectivity across multiple environments, AWS Transit Gateway facilitates efficient communication between VPCs and on-premises networks while maintaining strict security controls. This allows your data to flow securely and seamlessly, regardless of its origin or destination.
Moreover, AWS Firewall Manager offers centralized oversight, enabling the implementation and management of firewall rules across your entire AWS organization. This consistency in policy enforcement not only strengthens your security posture but simplifies compliance with industry regulations.
Data Protection and Encryption
Encryption plays a crucial role in this strategy. AWS offers built-in encryption capabilities across various services, ensuring that your data remains secure. For data at rest, services like Amazon S3 and Amazon EBS allow for server-side encryption, automatically encrypting data before it is written to disk. This means sensitive information is always stored securely, with options to use AWS Key Management Service (KMS) for managing encryption keys seamlessly.
For data in transit, AWS uses industry-standard protocols, such as TLS (Transport Layer Security), to protect information as it moves across networks. This safeguards against eavesdropping and tampering, ensuring that data remains confidential and unaltered during transmission.
Additionally, AWS provides AWS Backup, a centralized solution for automating and managing backup processes across AWS services. This not only protects your data but also ensures that you can quickly recover it in the event of loss or corruption, further enhancing your organization’s resilience.
Monitoring and Logging
In the realm of cloud security, effective monitoring and logging are vital for maintaining visibility and control over your environment. AWS equips organizations with powerful tools that provide real-time insights and facilitate proactive security management.
Amazon CloudWatch is at the forefront of AWS monitoring capabilities. It enables you to collect and track metrics, logs, and events, offering a comprehensive view of your AWS resources. With customizable dashboards and alerts, you can quickly identify anomalies and performance issues, allowing for immediate response and remediation.
Complementing CloudWatch, AWS CloudTrail serves as an essential logging service that records all API calls made within your AWS account. This creates a detailed audit trail, giving you visibility into who accessed what and when. CloudTrail logs are crucial for compliance investigations, helping organizations track user activity and identify potential security incidents.
Moreover, integrating Amazon GuardDuty enhances your monitoring strategy by providing intelligent threat detection. Utilizing machine learning and anomaly detection, GuardDuty continuously analyzes your AWS accounts and workloads for suspicious activity, alerting you to potential threats before they escalate.
Incidents Response
AWS Incident Response begins with preparation. AWS provides services such as AWS Security Hub, that aggregates and prioritizes security findings from across your AWS accounts and services. This centralized view equips security teams with the necessary insights to assess the security posture of their environment and make informed decisions.
When an incident occurs, having predefined runbooks and playbooks is essential. AWS recommends establishing clear procedures that outline the steps to take during different types of incidents, ensuring that your response team can act swiftly and efficiently. Utilizing tools like AWS Systems Manager, you can automate incident response processes, reducing manual intervention and minimizing response times.
After an incident is contained, the focus shifts to recovery and analysis. Services like AWS Backup can facilitate quick restoration of affected systems and data, allowing your organization to resume normal operations as soon as possible. Additionally, leveraging AWS CloudTrail logs provides crucial insights into the incident, enabling thorough post-mortem analyses that help refine your incident response strategy and improve future resilience.
Ultimately, an effective incident response plan, coupled with AWS’s powerful tools, empowers organizations to respond to security incidents with agility, reducing the potential impact on their operations and reputation.
Application Security
AWS Web Application Firewall (WAF) is a critical component in safeguarding your applications. It enables you to create custom security rules that filter and monitor HTTP requests, effectively blocking malicious traffic before it reaches your application. With the ability to protect against common web exploits such as SQL injection and cross-site scripting (XSS), AWS WAF helps ensure that your applications remain resilient against evolving threats.
AWS Shield, a managed Distributed Denial of Service (DDoS) protection service, complements AWS WAF by providing advanced threat detection and mitigation for your applications. By automatically defending against DDoS attacks, Shield ensures that your applications maintain availability and performance, even during an attack.
Furthermore, integrating AWS CodePipeline and AWS CodeBuild into your development workflow enhances application security from the ground up. By implementing continuous integration and continuous deployment (CI/CD) practices, security measures can be embedded into the development lifecycle. This includes automated security testing and vulnerability scanning, allowing you to identify and remediate vulnerabilities before your applications go live.
Finally, incorporating AWS Secrets Manager helps securely store and manage sensitive information, such as API keys and database credentials, ensuring that your applications access this information without exposing it in your codebase.
Conclusion
As the reliance on digital assets grows, securing these assets is more critical than ever. The sharp increase in data breaches underscores the need for organizations to implement comprehensive security strategies tailored to the cloud. By leveraging AWS’s extensive security tools and following best practices, businesses can establish a strong infrastructure that safeguards their data and operations against emerging threats.
The Shared Responsibility Model clarifies the distinct roles of AWS and your organization, enabling you to take charge of your security measures while benefiting from AWS’s dependable infrastructure. From effective IAM management to essential network security measures, data encryption techniques, and thorough monitoring and logging, each component plays a vital role in enhancing your security posture.
Ultimately, prioritizing cloud security is not just about protecting information; it is about building trust with customers and stakeholders. As you navigate the complexities of securing your AWS environment, remember that a proactive and well-rounded approach is essential for ensuring your organization’s resilience in today’s ever-changing digital landscape. Embracing AWS’s security features empowers your organization to confidently face the challenges of an evolving threat landscape.






